Solutions
Law firms
Tax, audit & accounting firms
Success stories
-
A true competitive advantage
Law firm Zarwin Baum’s embrace of generative AI as the natural next step in the evolution of legal work and their adoption of CoCounsel Legal has helped them achieve remarkable efficiency gains and improved client relationships.
-
Workflow transformation drives impact
Brinks, a global leader in secure logistics and security solutions, used CoCounsel to reimagine what was possible with AI tools, turning legal challenges into a competitive advantage.
-
The forefront of audit tech
A better auditing workflow solution was the answer to multiple challenges faced by The Mercadien Group. Find out how they achieved greater efficiency by embracing Cloud Audit Suite.
Products
Legal
Trade & supply
Tax, audit & accounting
- 1040SCAN
- Audit Intelligence Analyze
- CoCounsel Audit
- CoCounsel Tax
- Ready to Advise
- Ready to Review
- View all
Corporate tax
Recommended products
-
CoCounsel Legal
Transform your work with the only AI legal solution uniting research, drafting, and document analysis in a single experience. Designed by legal experts and built on trusted content and advanced AI, CoCounsel Legal accelerates multistep work so you can better serve your clients and grow your business.
-
CoCounsel Tax
Transform your tax practice with CoCounsel Tax, an AI-powered assistant that combines trustworthy answers, automation, and firm knowledge into one seamless platform. Enhance efficiency, reduce risk, and improve client confidence with CoCounsel Tax.
-
CLEAR
Powerful software designed for law enforcement, compliance, risk, and fraud investigators. Conduct thorough investigations with ease using our intuitive online investigation software. Efficiently, prevent, detect, and solve crime.
Purchase
Buy solutions
Resources
Insights
Events
Product training
Product communities
Developers
Highlights
-
2026 SKILLS showcase
Join weekly sessions to experience in-depth demonstrations of the leading legal AI products while connecting with strategic law firm leaders in knowledge management, innovation, and AI.
-
Ghosts on the ledger
Payroll fraud is a major compliance risk. Learn how payroll analytics and AI-powered tools can help exorcise phantom employees and employers.
-
Future of professionals report 2025
The Thomson Reuters Future of Professionals Report 2025 reveals how AI continues to shape professional work — and what it takes to get ahead. This year’s report shows that increased efficiency, productivity, and cost savings top the list of benefits professionals attribute to AI, making it indispensable for organizations facing rapid change.
January 2025 release notes
What's new
Refresh token
- grant_type
- Required. Selectrefresh_tokenas the grant type.
- refresh_token
- Required. Provide the refresh token issued to you.
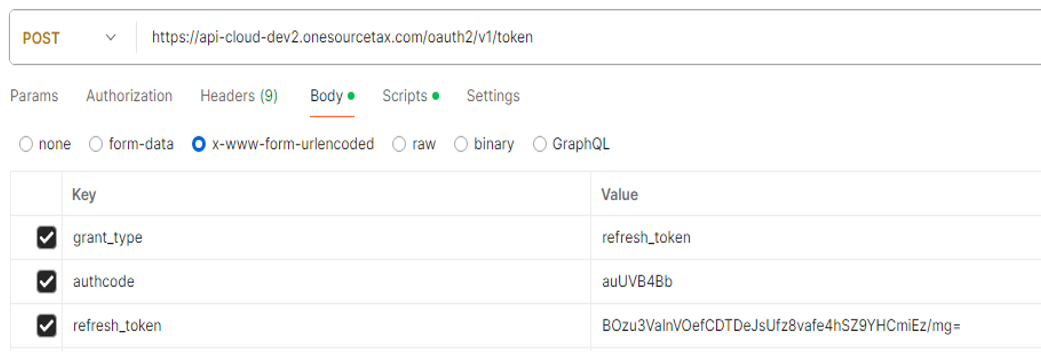
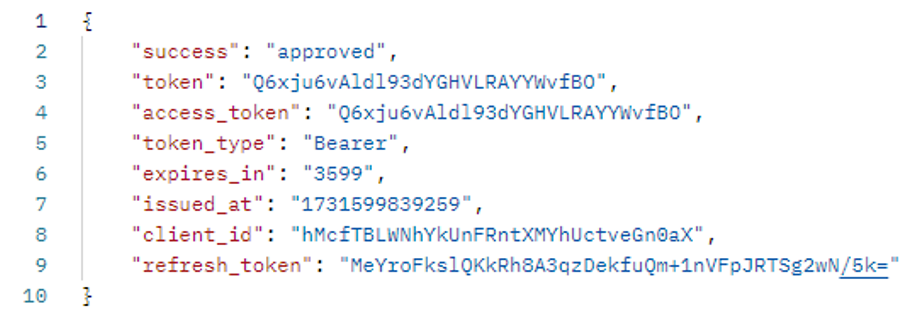
- An individual refresh token is valid for 24 hours. Use it within this time to avoid needing to request a new access token using the original method.
- The scopes remain the same. Omit them in subsequent calls using the refresh token grant type.
- You can use a refresh token once to generate a new access token. Then, use the new refresh token from the response.
- Refresh tokens are typically long-lasting credentials used to request additional access tokens. They link specifically to the client who receives them. If your client type is confidential or has credentials (or other authentication requirements), authenticate with the authorization server.
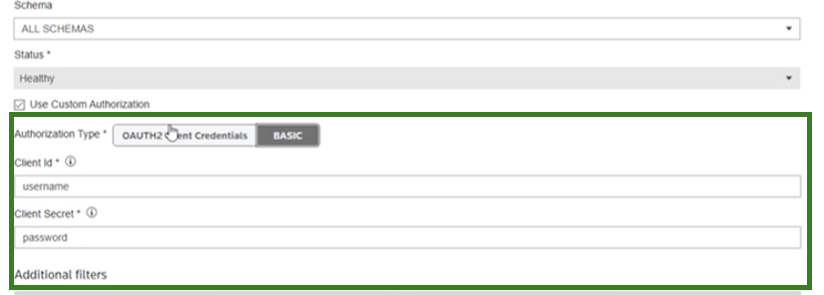
Basic authorization token
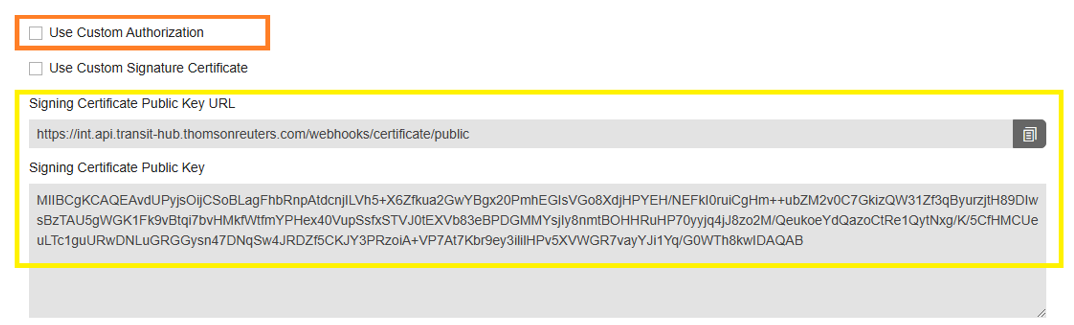
- Thomson Reuters signed JWT Bearer tokenThis is the default option. With every call to your callback, we generate a JWT token and sign it with a special certificate. You can validate the token signature using the provided public key (which you can download from a special URL or copy from ONESOURCE Events).
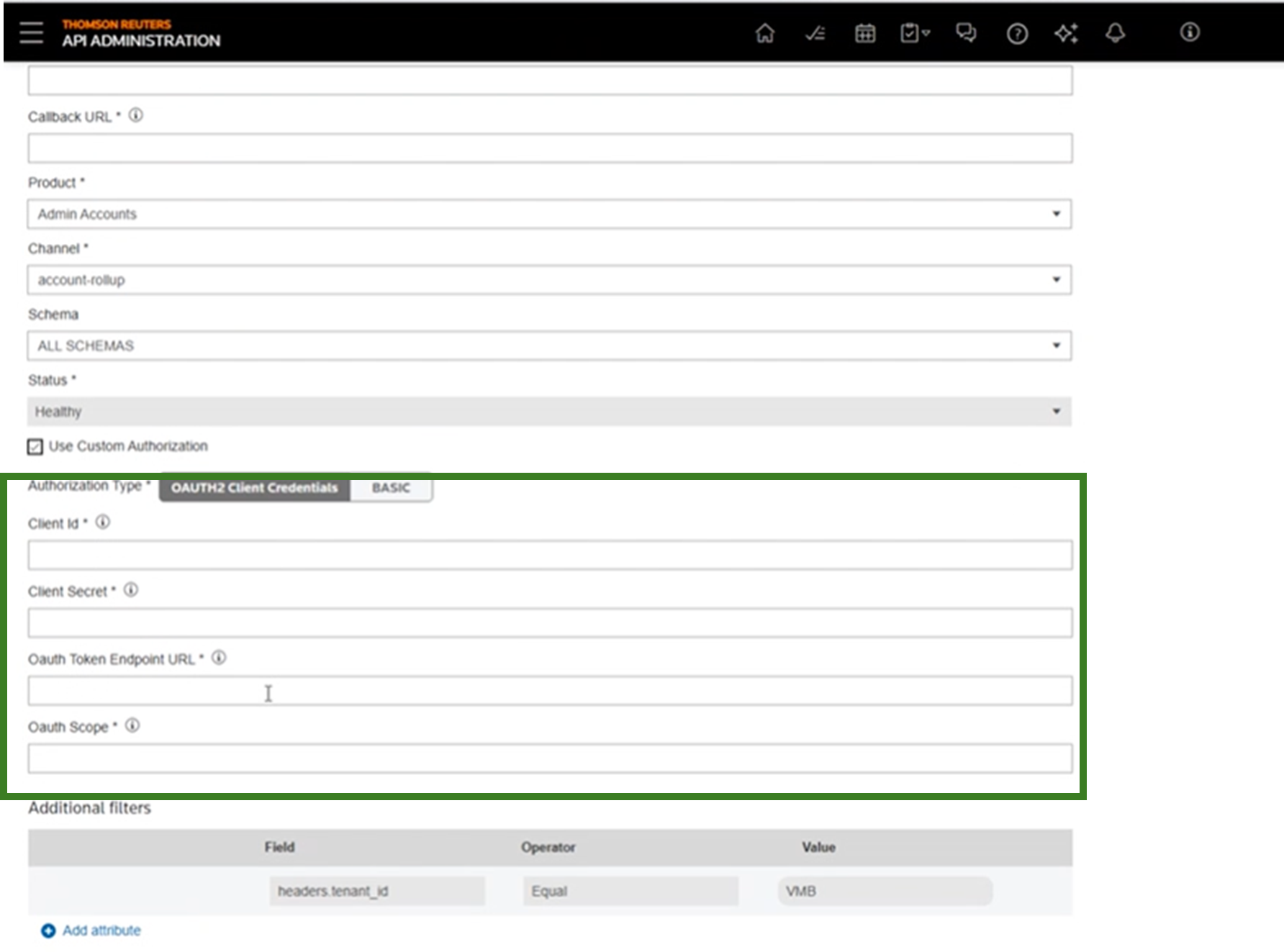
- Oauth2 CredentialsYou can set up your own identity provider and share the OAuth2 token endpoint and credentials with us. We’ll request an access token and provide it with all calls to your callback endpoint. We'll cache the access token value depending on its expiration time.
- Basic AuthorizationThis is the simplest and least secure authorization method. You provide a username and password during endpoint setup. We provide these credentials with every call to your callback as an Authorization HTTP Header in the following form:Authorization: Basic base64encoded(username: password)
This article applies to:
- Product: ONESOURCE API Administration
